| Table of Contents |
|---|
System Configuration
As Admin user you will find the E2EE settings in the Encryption section of the Admin Settings.
...
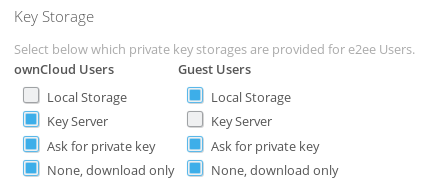
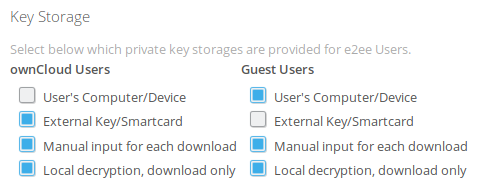
Select, which key storages will be available for your users. You may provide different settings for ownCloud and guest users.
| Note |
|---|
If you provide more than one key storage options, users must set up their key storage in their personal settings prior to being able to read and save encrypted files. This must be communicated in advance to avoid any confusion. |
...
There is a clear trade-off between security and usability, depending on which option you want:
| Description | Usability | Local Storage | Security | |||
|---|---|---|---|---|---|---|
| User's Computer/Device | The private key is stored in the browser local storage (similar to a cookie) | |||||
| External Key Server/Smartcard | The private key is available through an external process running on the client machine. Then the browser can only request decryption.
| Ask | ||||
| Manual Input for each download | When downloading an E2EE file, the private key has to be copy/pasted into a browser form. The key is never saved in the browser. | |||||
| Local decryption, download only | The E2EE file is downloaded locally and a secondary tool is required to decrypt (E2EE Reader). The E2EE Reader supports both file and Smart Card decryption (currently Windows only). The key is never saved in the browser. |
General remarks about security:
...
To see exactly how many users are enabled to use the E2EE app, you may click the Apply E2ee Groups. After a reload the Summary section shows the number of currently enabled users.
Enforce End-To-End-Encryption
You may configure a system wide setting where it is only allowed to upload e2ee files. To enable, set the e2eeshare key enforced_e2ee to true in your config.php. When you want to exclude some groups from this behavior, add them comma separated as value for enforced_excluded_groups.
A configuration snippet with e2ee enforced and the groups admin and helpdesk excepted looks like below
| Code Block | ||||
|---|---|---|---|---|
| ||||
'e2eeshare' =>
array (
'enforced_e2ee' => true,
'enforced_excluded_groups' => 'admin,helpdesk'
), |
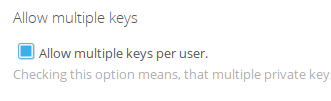
Multiple Keys
Users can only have one public key assigned to them by default. This is a security feature. If you want users to have multiple keys (i.e. one for each of their device or for backup purposes) you may enable this option.
Server-Side Encryption
For those cases where it is necessary that users can upload files via ownCloud client to an e2ee encrypted share, there is an option to permit uploads of unencrypted files.
In that case any files dropped into a local folder will be sent unencrypted to the server. When https is enabled for the site the upload will be still encrypted via Transport Layer Security. The file on the ownCloud server is encrypted immediately and the original contents is replaced. The original upload is unencrypted on the ownCloud server for a very short time however. This is a convenience feature an administrator has to weigh up based on business requirements.
To enable this feature check the box Permit upload of unencrypted files.
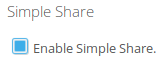
Simple Share
To simplify the end-to-end-encryption workflow, a private key can be created when sharing with a new user. This private key will be stored AES encrypted in the database and new users will receive an email with the password.
Upon first login new users unlock the initial private key with the password and a new key pair will be created. Shared files are reencrypted with the new key on the fly and the initial private key will be deleted.
The password itself is only delivered by email and never stored.
| Info |
|---|
Simple Share requires the key storage User's Computer/Device enabled for both guests and ownCloud users. It cannot be enabled unless both of the storages are enabled. |
| Note |
|---|
Be sure that the share recipients have got valid email addresses (check the Users page) or the email providing the private key password can never be sent. This affects ownCloud users only since for guest users the email address is required for invitation. |
| Info |
|---|
When a user did not receive or lost the password for the initial private key it cannot be resent. To have the user receive a password again, remove all shares with this user and recreate them. Then a new initial private key will be generated and the new password will be sent to the user. |
To enable this feature check the box Enable Simple Share:
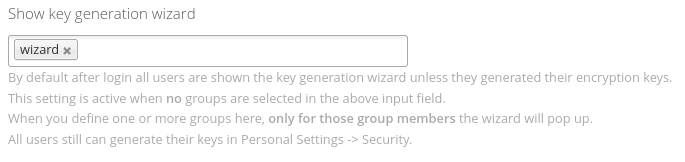
Wizard Visibility
By default, after login, all users are shown the key generation wizard unless they generated their encryption keys.
There is an option to only show this wizard to certain group members. Define one or more groups in Show key generation wizard, then only for those group members the wizard will pop up.
All other users still can generate their keys in Personal Settings -> Security.
Status Report
You can generate a status report of your E2EE installation by clicking the button in the Summary section: The report will be mailed to the logged in administrator's email address. It includes the current license information such as the number of enabled users.
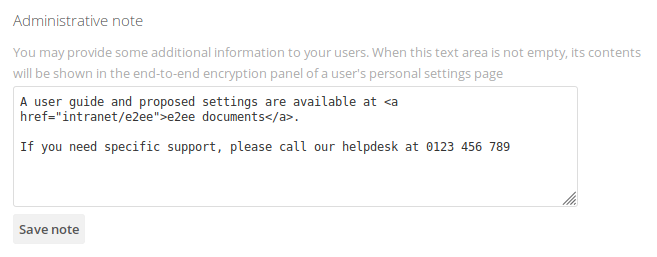
Administrative Note
This functionality provides an information text area which is shown on top of every users' E2ee Section in the Personal Settings. You may use this, for instance, for a detailed guide about the setup or contact information.
When the text area is left blank, nothing will be shown.
occ Commands
As an administrator you might want to perform certain operations by using scripts. The following commands are available:
e2eeshare:list-keys
Show all public keys for the provided user
| Code Block | ||||
|---|---|---|---|---|
| ||||
sudo -u www-data php occ e2eeshare:list-keys <user> |
e2eeshare:add-key
Add a new public key to provided user
| Code Block | ||||
|---|---|---|---|---|
| ||||
sudo -u www-data php occ e2eeshare:add-key <user> <local-path-to-public-key> |
e2eeshare:delete-key
Delete a public key from provided user
| Code Block | ||||
|---|---|---|---|---|
| ||||
sudo -u www-data php occ e2eeshare:delete-key <user> <key id> |
e2eeshare:encrypt-folder
Convert an unencrypted folder to an e2ee encrypted folder.
| Code Block |
|---|
sudo -u www-data php occ e2eeshare:encrypt-folder <user> <path> |
where path is absolute from a user's root directory, e.g. /Documents